Background – a voluntary approach
The US National Institute of Standards and Technology’s (NIST) voluntary cyber security framework (CSF) is designed to boost the resilience of critical infrastructure in the private sector.
The NIST framework does not impose any regulatory compliance standards: the NIST talks about organisations “choosing to leverage” the framework, rather than being “required to comply” with it.
At a basic level, the CSF can be seen as an attempt to encourage organisations to treat their cyber security risks as seriously as they do their other operational risks (e.g. financial, supply chain or personnel).
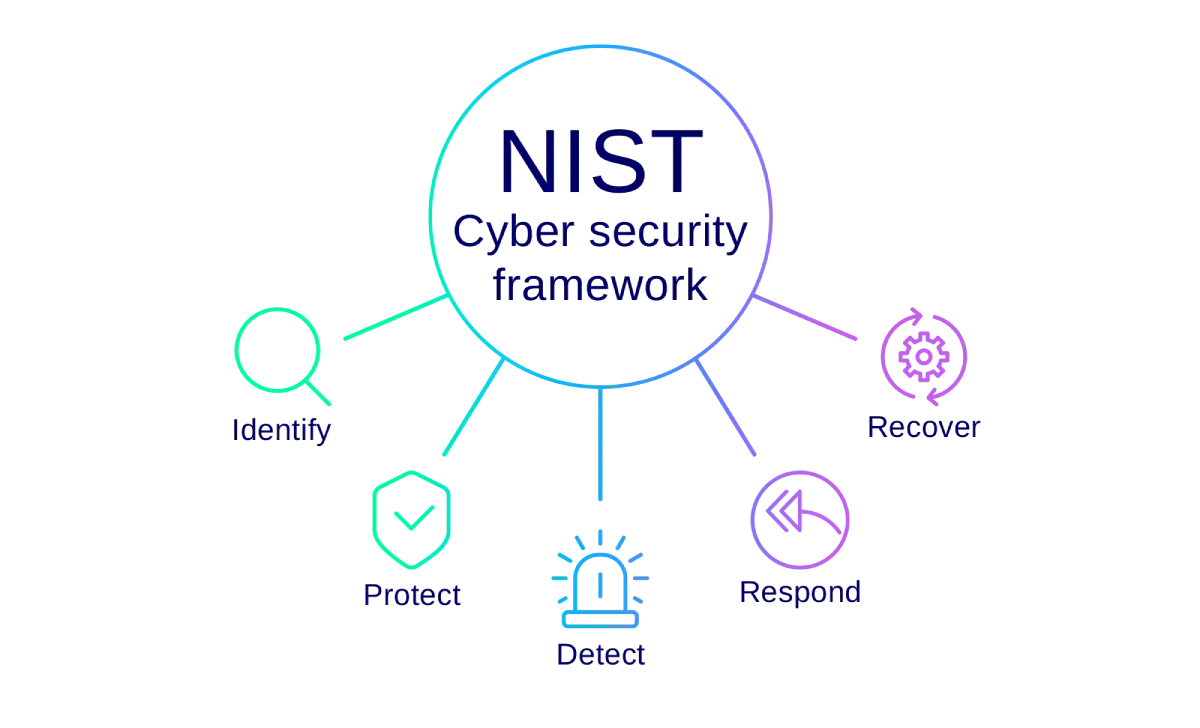
The single, overarching aim of what the NIST describes as the framework’s ‘five core functions’ is to give an organisation a strategic overview of its cyber security risks:
Identify –understand how to manage cyber security risks (to data, systems, assets, etc).
Protect – safeguarding measures are in place to ensure the delivery of critical infrastructure services.
Detect – an organisation can clearly define how it identifies cyber security incidents.
Respond – an organisation has a plan for dealing with various cyber security incidents.
Recover – an organisation has a plan for operational resilience, including a prioritised list of functions/services and a course of action for repairing affected systems.
Common use cases for the CSF
Creating a baseline of existing capabilities
The first step for most organisations should be to understand their existing cyber security capabilities. Cyber security is a broad field, which means that most organisations tend to narrow their focus to those aspects that are of natural interest to, or within the comfort zones, of their people. Using the CSF allows an organisation to reduce this level of bias and assess all its capabilities in a structured and logical manner, and identify the baseline of its existing capabilities.
A baselining activity is common practice when a security team gets new leadership, and the outcome will frequently form the foundation on which 90-day and multi-year plans are built. A review by an external organisation provides the focus, leverage and details that are required by new leadership, and is something that all new CISOs (or equivalent) should consider when designing their cyber transformation roadmap.
Building a cyber transformation roadmap
NIST framework-based baselining can help you to design a transformation roadmap by ensuring effective planning and capability development. The transformation roadmap itself is a useful way of understanding the costs associated with capability development and security improvements and explaining these requirements to the board.
Reporting on cyber maturity to the board
A consistent message, concisely conveyed, is key to achieving engagement with your board.
The CSF is a useful way to break cyber security into six categories that can be broadly understood by anyone, no matter what their professional background. We often see the six categories combined with maturity scores, which allows for comparisons with peer organisations and the quick identification of areas that require more attention and investment.
Assessing post-acquisition integration needs
Integrations are challenging and present significant risks to organisations.
The CSF has been used as a mechanism for consistently assessing third parties and ensuring appropriate capabilities are identified, understood, and aligned prior to integration. The use of the CSF has allowed teams working on different phases of an acquisition to make direct comparisons between organisations.
The consistent terminology and mapping of all outputs to a common framework enables the reuse of the information collected during the fast-moving due diligence phases, thus providing the basis for post-acquisition reviews and decision making.
If an organisation does not map to a framework, it is common to see repetition of common controls at the different phases. This, in turn, leads to inefficiencies, duplicated work and frustration for key stakeholders – increasing the risk of human resources issues at a critical time for the organisation.
Quantifying cyber risk with the NIST CSF assessment
NIST’s CSF enables a holistic assessment of your cyber capabilities and an in-depth understanding of your key cyber security challenges and issues. The output of the CSF assessment can act as one of the key inputs into a cyber risk quantification framework.
Examples of organisations leveraging the CSF
Organisation profile | A music copyright collective | Global IT and IT-enabled service (ITES) organisation | Fintech organisation |
|---|---|---|---|
Organisational challenge | The board was uneasy about cyber security adoption after an internal incident. It wanted to assess the current state of its cyber security and create a roadmap for cyber transformation. | Acquisition was a cornerstone of the organisation’s growth strategy. For each acquired target, the organisation’s CSO wanted cyber security capabilities assessed to enable a like-for-like comparison and to inform the integration roadmap. | The organisation’s CEO was looking for an external partner to work with the Security officer to holistically improve cyber security and take risk-aware decisions. |
How the CSF was used to address the challenges | A maturity assessment based on the NIST’s CSF was conducted. The target maturity score was based on peer benchmarking and the organisation’s threat landscape. It formed the basis for a detailed cyber transformation roadmap. | A light-touch NIST CSF assessment was conducted as part of pre-deal cyber due diligence (PDCDD). The PDCDD report was further augmented by a post-deal cyber maturity assessment (PDCMA), again based on the NIST CSF. The report findings allowed for the creation of an integration roadmap and related budget. As one of the key reporting metrics, the CSO compared their organisation to its acquired organisations, using the PDCMA. | An NIST CSF maturity assessment was agreed with the COO. A NIST CSF maturity assessment was conducted with the input of the CSO to assess the current state, target state and tasks for achieving the roadmap’s aims. These aims were included in the CSO’s reporting to the CEO and COO. Based on the maturity assessment, cyber risk quantification was conducted for both ransomware and DDoS attack scenarios, leveraging elements of the FAIR model. Increase in maturity and decrease in quantified risk was included in reporting to the CEO/COO. |





